How to install and configure Redis on Ubuntu
Redis is an open-source in-memory key-value data store. It can be used as a database, cache, message broker and supports various data structures such as Strings, Hashes, Lists, Sets, etc... Apart from its performance and flexibility, Redis stands out with its wide language support, high availability, and automatic partitioning.
Installing Redis server
The Redis packages are available under the default apt repository. Run below command from the terminal to install Redis on your machine:
sudo apt-get update && sudo apt-get install redis-server
This will download and install Redis and its dependencies.
Configuring Redis server
Once the installation is completed, there is one important change to make in the Redis configuration file (with nano or any other editor):
sudo nano /etc/redis/redis.conf
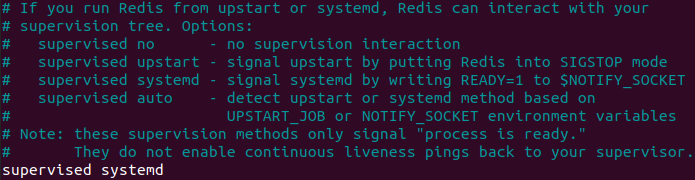
Inside the file, find the line specifying the supervised directive. By default, this line is set to no. However, to manage Redis as a service, providing you with more control over its operation, set the supervised directive to systemd:
You can also update the following values in Redis configuration file according to your requirement.
maxmemory 256mb
maxmemory-policy allkeys-lru
The above configuration tells Redis to remove any key using the LRU algorithm when the max memory of 256mb is reached. You can increase max memory limit as per available on your server. Save the changes, close the file and restart Redis:
sudo systemctl restart redis.service
Testing Redis
First of all, let's check if the service is correctly running:
sudo systemctl enable redis-server.service
You should see something like this:
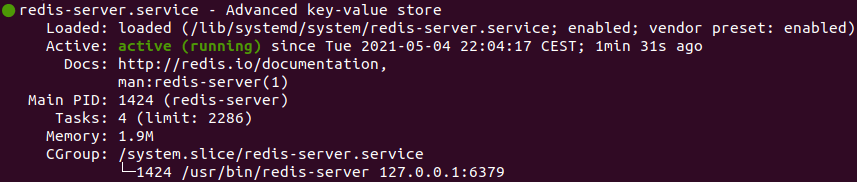
Here, you can see that Redis is running and is already enabled, meaning that it is set to start up every time the server boots. To test that Redis is working correctly, connect to the server using the command-line client:
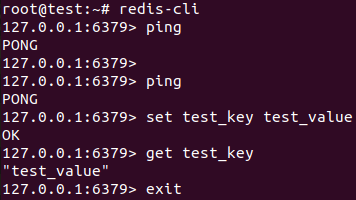
redis-cli
Now you can run some basic commands to test it:
Securing Redis (recommended)
Redis includes an authentication feature as an additional security layer. The feature is not enabled by default. It’s important that you specify a very strong and very long value as your password. Rather than make up a password yourself, you can use the openssl command to generate a random one:
openssl rand 80 | openssl base64 -A
It will output long and secure password option. Once more, open the Redis configuration file:
sudo nano /etc/redis/redis.conf
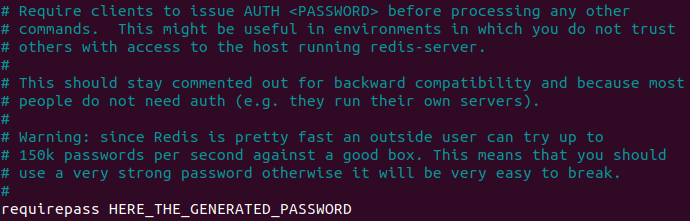
Locate the requirepass directive and put the generated password as value:
Save the changes, close the file and restart Redis:
sudo systemctl restart redis.service
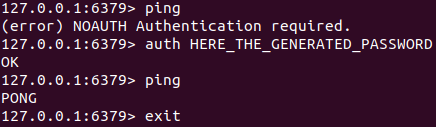
As soon as the password is set, redis-cli commands will stop responding until you authenticate with auth command providing your password:
Allowing remote connections (optional)
By default, the Redis server does not accept remote connections. If we have an application that needs to establish a connection with our external Redis, we need to change some configuration lines on the Redis server:
sudo nano /etc/redis/redis.conf
Navigate to the line that begins with the bind directive:
bind 127.0.0.1 ::1
By default, this value is set to 127.0.0.1 ::1, meaning that the server will only look for local connections. You will need to update this directive with an external IP address, list of IP addresses (separated with space) or comment the line to allow any IP connection.
Save the changes, close the file and restart Redis:
sudo systemctl restart redis.service
To check that this change has gone into effect, run the following netstat command:
sudo netstat -lnp | grep redis
You should see something like below showing the IP addresses which Redis server is listening to:
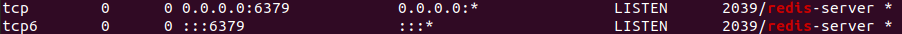
In order to test the connection redis-cli provides host parameter to establish connections with specified IP address:
redis-cli -h <REDIS_IP_ADDRESS>
Renaming dangerous commands
Another way to protect your data is to disable specific commands or rename them, so they are unguessable. When run by unauthorized users, such commands can be used to reconfigure, destroy or even erase your data. This is a useful security feature that also can restrict normal users from using commands that could harm the system.
Open the Redis configuration file and navigate to the SECURITY section:
sudo nano /etc/redis/redis.conf
Some of the commands that are considered dangerous include: FLUSHDB, FLUSHALL, KEYS, PEXPIRE, DEL, CONFIG, SHUTDOWN, RENAME, DEBUG, etc...
If you know you will never use a command that could be abused, then you may disable it:
rename-command FLUSHDB ""
Otherwise, it might be in your best interest to rename it:
rename-command FLUSHDB NEW_NAME_FOR_FLUSHDB
After renaming a command, apply the changes by restarting Redis:
sudo systemctl restart redis.service
Conclusion
You installed, configured and tested your Redis server. You also used its built-in security features to make it less vulnerable to attacks. Now you can start using the features it offers, learn about different data types it has and check how fast it works.
We strongly recommend you to setup a good firewall protection on your Redis server for increased security.




0 Comments