Global DDoS attack hits 3.8 Tbps
During a large-scale distributed denial-of-service (DDoS) campaign targeting the financial services, internet, and telecommunications sectors, attacks reached an unprecedented peak of 3.8 terabits per second (Tbps), the highest recorded to date. This month-long assault consisted of over 100 hyper-volumetric DDoS attacks, which inundated network infrastructure with vast amounts of garbage data.
The mechanics of a volumetric DDoS attack
Volumetric DDoS attacks work by overwhelming the target with enormous volumes of data, leading to bandwidth consumption and resource exhaustion of applications and devices, ultimately cutting off access for legitimate users. Many attacks aimed at the network’s infrastructure exceeded two billion packets per second and three terabits per second, particularly affecting network and transport layers (L3/4).
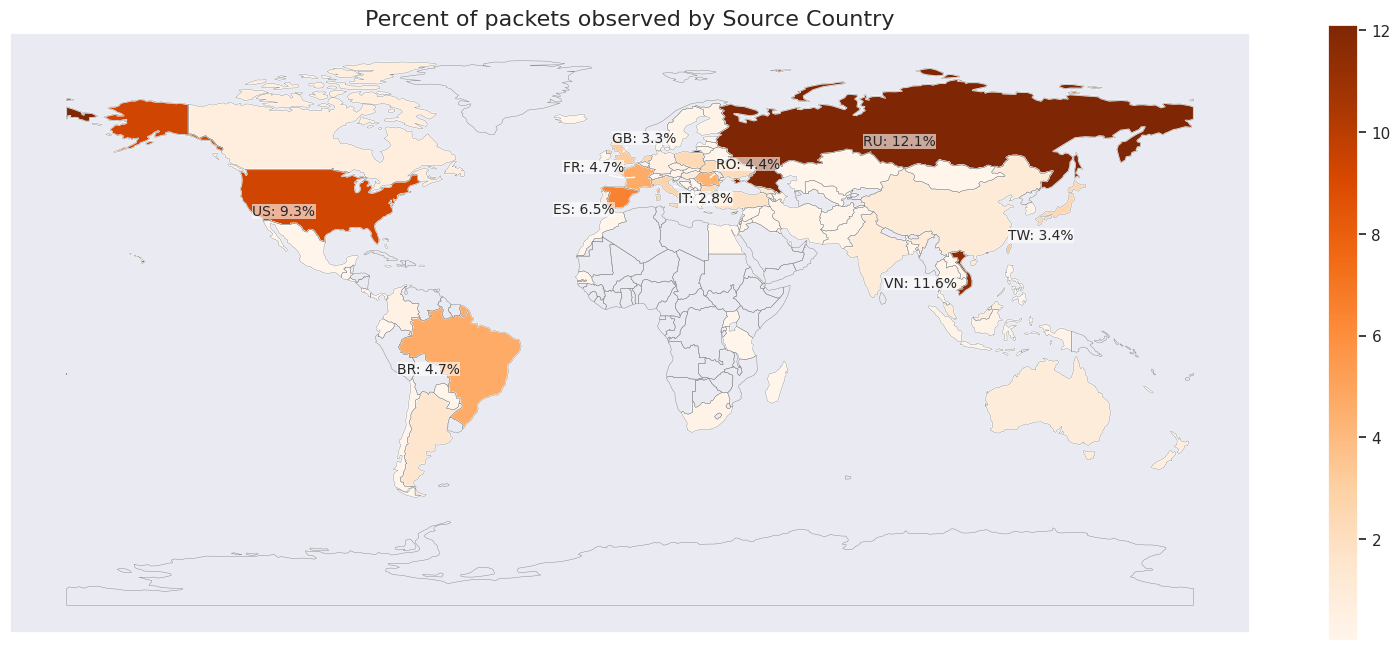
According to Cloudflare researchers, the compromised devices were globally distributed, with concentrations in countries like Russia, Vietnam, the U.S., Brazil, and Spain. These devices, which included Asus routers, MikroTik systems, DVRs, and web servers, were exploited using the User Datagram Protocol (UDP), known for its fast data transfer speeds and lack of a formal connection.
Before this record-breaking attack, Microsoft had held the defense record for mitigating a 3.47 Tbps attack against an Azure customer in Asia. Most DDoS attackers use botnets, or networks of infected devices, to launch these attacks or exploit methods to amplify data delivery. A report from Akamai also confirmed that newly disclosed CUPS vulnerabilities in Linux systems could be another major vector for future DDoS campaigns, with over 58,000 systems vulnerable.
Conclusion
While Cloudflare successfully mitigated the attacks autonomously, including one that peaked at 3.8 Tbps lasting for 65 seconds, these incidents highlight the evolving threat posed by DDoS campaigns. With attackers continuously exploring new methods and vulnerabilities, organizations must remain vigilant and prepared to defend against these large-scale disruptions.


0 Comments